Who doesn’t know the struggle? Buying an interesting piece of hardware for a song and a dance, and then finding that the device’s firmware and/or configuration file is locked down with various encryption or obfuscation methods. This was the experience [Ali Raheem] had when he got a TP-Link TL-MR3020 V3 for a mere 18 British Pounds, intending to use this 4G-capable router to increase internet reliability.
Naturally this can all be done when staying inside the vendor-provided marked lines, which in this case meant ignoring the encrypted configuration files. As the owner of the hardware, this was of course unacceptable and thus [Ali] got a firmware image from the TP-Link site to see what could be gleaned from it in terms of encryption keys and other hints.
After obtaining the TP-Link-provided BIN file, the application of binwalk helpfully extracted the files embedded in it, followed by John the ripper decrypting the passwords in the /etc/passwd.bak file, and ultimately finding the encrypted /etc/default_config.xml file. Searching for this filename string in the rest of the extracted files led to /lib/libcmm.so.
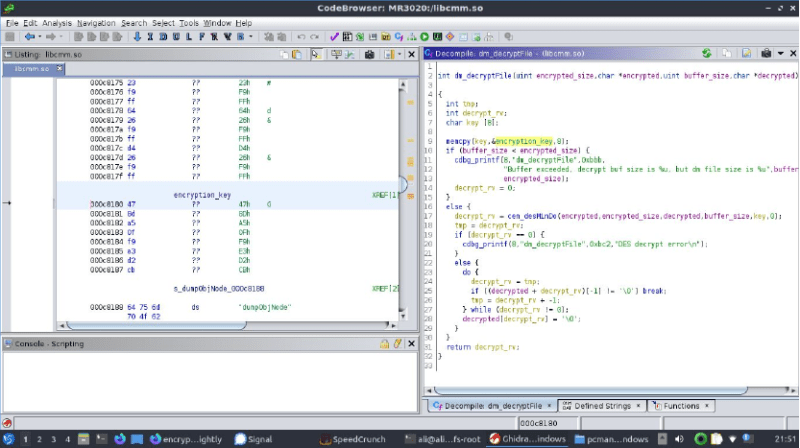
Dropping this shared library file into Ghidra to disassemble its code, [Ali] found a function suspiciously called decryptFile. Inside was a reference to the global key string, which when tossed into OpenSSL and after some fiddling turned out to decrypt the XML configuration file in des-ecdb mode. From this point dropping in one’s own configuration files should be no problem after encrypting them to make the firmware happy. Nice work!
0 Commentaires