
The saying “time and tide wait for no man” is usually used as a verbal kick in the pants, a reminder that sometimes an opportunity must be seized quickly before it passes by. But it can also be interpreted as a warning about the perpetual march of time and how it impacts the world around us. In that case, we would do well to add cellular technology to the list of proverbial things that wait for no one. Do you need 5G? No. Do you want it? Probably not. But it’s here, so be a good consumer and dump all your 4G hardware in the name of technical progress.
This line of logic may explain how the Verizon-branded Netgear AC791L 4G “Jetpack” hotspot you see here, despite being in perfect working order, found itself in the trash. The onset of 5G must have been particularly quick for the previous owner, since they didn’t even bother to wipe their configuration information from the device. In the name of journalistic integrity I won’t divulge the previous owner’s identity; but I will say that their endearing choice of WPA2 key, iluvphysics, makes for a nice fit with our publication.
A quick check of eBay shows these devices, and ones like it, are in ample supply. At the time of this writing, there were more than 1,500 auctions matching the search term “Verizon jetpack”, with most of them going for between $20 and $50 USD. We like cheap and easily obtainable gadgets that can be hacked, but is there anything inside one of these hotspots that we can actually use? Let’s find out.
A Tidy Package
As far as first impressions go, the Verizon Jetpack certainly doesn’t disappoint. The handheld unit has a very pleasing heft to it, and the front and back surfaces have a slightly rubberized finish reminiscent of a Thinkpad’s lid. I especially like the two small sliding doors on the bottom of the unit that cover up the external antenna ports. While a dedicated “Back” button would make navigating the user interface a bit more streamlined, the capacitive touch buttons on the front work well, and the screen is quite nice.


Opening up the device we can clearly why it’s so heavy: the massive 4,340 mAh lithium ion battery weighs in at 87 grams, compared to 75 g for the hotspot itself. This might seem like an excessive amount of power, even for what amounts to a 4G modem paired with a simple wireless router, but the manual explains that the Jetpack can double as a USB battery bank. Though the lack of a female USB Type-A on the unit means you’d need to carry a little USB On the Go (OTG) adapter to charge other gadgets.
Under the Hood
Ten T4 screws hold the back panel of the Jetpack on, and while they did get cute and put a sticker over one of them to rat out the owner should they dare to explore their own hardware, there was no problem getting the unit open. With the direction mobile electronics have taken in the last few years, I was somewhat worried the whole thing would have been glued together.
With the rear off, we get a good look at the dual conformal antennas that curve around the edges of the device. These are connected to the PCB with some springy tabs, which in turn are directly connected to the external antenna ports. Compared to what passes for a cellular antenna in a modern ultra-slim smartphone, the Jetpack offers a pretty impressive array of options in the reception department. Of course, being a 4G hotspot, the ability to pull in a solid LTE signal is pretty critical.
The PCB itself just pops right out of the frame, and beyond the spring contacts for the antennas, its only physical connection to the rest of the unit is the connector that goes to the front LCD and button assembly. It’s certainly not surprising that all the components on the board have been covered up with RF shields, as it’s something we’ve seen in other devices with cellular connectivity, but I was happy to find they weren’t soldered down at least. With a little careful prying, we can get a good look at the cornucopia of ICs within.
Built For Purpose
Oftentimes when we crack open a gadget like this, we’re able to find some familiar chips inside. Whether it’s a Z80 or an STM32, these well-known components provide a tangible link between the hacking community and the consumer hardware world. Not just ideologically, but practically, as identifying the MCU at the heart of a device is the first step towards coming up with your own replacement firmware for it.
I’d like to tell you that some common piece of silicon was hiding under one of those RF shields, and that running your own code on the hardware is just a matter of figuring out the proper OpenOCD settings. But unfortunately, that’s not the case.

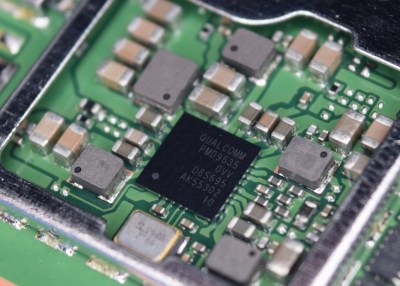



Instead we’ve got a whole mess of tiny ICs, most of which are unsurprisingly from Qualcomm and clearly intended for mobile phones. The WTR3925 is a cellular transceiver, vintage 2013 or so, and the MDM9630 is an LTE modem. The QCA6174 appears to be responsible for the WiFi and Bluetooth interfaces of the Jetpack, and the RF7459 is a CDMA amplifier. The SMB1356 is the charge controller for the battery, while the PMD9635 is a power management IC which apparently was also used in some variants of the iPhone 6. I wasn’t able to ID the large chip, labeled GP1639, but my guess is that’s the SoC that’s pulling it all together.
While I was able to find basic descriptions of most of the Qualcomm chips inside the Jetpack, actually getting a full datasheet on any of these components is another story entirely. The situation is a bit reminiscent of the time I attempted to research some of the components in the VeriFone MX 925CTLS payment terminal, but wasn’t able to find much more than vague descriptions and stock levels online. It seems like the folks working on these state-of-the-art telecommunications devices are in a fairly tight-knit club, and hackers like us aren’t invited.
Putting it to (Re)Use
While impossible isn’t a word we like to use around these parts, the chances of getting your own code running on the Jetpack doesn’t look great. There’s a lot of secrecy surrounding the hardware that goes into modern phones, and even though these chips are far from the cutting edge in 2021, public information about them isn’t exactly forthcoming. It’s also a pretty safe bet that any effort to reverse engineer the SoC will eventually run into some insidious security countermeasures.
So is the Verizon AC791L Jetpack a dead-end? Maybe not. While the internal dimensions aren’t terribly forgiving, I could certainly see the main board of this device replaced with a custom PCB carrying an ESP8266 or ESP32. Tapped into the Jetpack’s antennas and ample battery, you’d have a great platform for mobile WiFi hacking and experimentation. For that matter, it would be an exceptionally discreet device for penetration testing. It might not be worth paying ~$30 USD for one of these things just to use its battery and enclosure, but if you happen to find one in the trash like I did, you might have a nice winter project on your hands.

0 Commentaires