
By now it’s probable that most readers will have heard about LastPass’s “Security Incident“, in which users’ password vaults were lifted from their servers. We’re told that the vaults are encrypted such that they’re of little use to anyone without futuristic computing power and a lot of time, but the damage is still done and I for one am glad that I wasn’t a subscriber to their service. But perhaps the debacle serves a very good purpose for all of us, in that it affords a much-needed opportunity for a look at the way we do passwords.
What Does A Car Ferry Have In Common With A Password?

One of my favourite ways to leave the UK is the ferry from Harwich to Hoek van Holland. There’s an odd difference between its two legs though, the UK end has airport style security with metal detectors and x-rays, while at the Hoek I simply walk through passport control onto the ferry.
It’s a particularly egregious demonstration of security theatre, the practice of overdoing largely unnecessary security measures to appear to be doing something. In the case of a car ferry it’s especially pointless to use measures on foot passengers designed to protect aircraft, when all the motorists simply drive onto the ferry unobstructed. A ferry might seem to have little relevance to password security, but the idea of security theatre it introduces is definitely of relevance in the field of passwords. How often have you encountered a website that imposes arcane rules on your choice, demanding a a specified length, that it must contain numbers, or even worse, special characters? Does this help much? I’m not convinced, and I’d like to take a little journey through the issue to find out.
Weak And Feeble Human Brains Are No Match For A Computer!
The ideal password is a long randomly-generated string designed to confound brute force cracking software. These techniques rely on trying every possible combination of characters sequentially, and the longest string with the most entropy is intended to be the one that takes the most time to reach. If you take the 95 printable ASCII characters as the alphabet, an attacker has to try 95 to the power of the string length different strings to catch everything, something that is likely to take a while. For a 10-character password that figure is 5.987369392 × 10¹⁹, you do use passwords that long, don’t you?
Unfortunately very few humans use random strings as their passwords. They aren’t memorable at all, and thus if your passwords are like this you’re probably using some kind of password manager for them. Real humans have an unfortunate propensity to behave in predictable ways rather than random ones, so they’ll use words and phrases they know and remember. And when asked to add letters, numbers, and special characters, they remain just as incapable of doing so in a random manner as they were with strings. A simple string such as jennylist becomes JennyList with capitals added, then JennyList! with a special character, and finally JennyList!1234 when it’s been padded out to fit. The developer trying to crack it can try short cuts such as given names, dog’s names, football teams, and birth years with common letter substitutions and numerical sequences, making these memorable passwords secure in appearance but with substantially reduced entropy. But it’s all OK folks, because they pass the test of having a special character, numbers, and upper-case letters.
Incorrect Horse Battery Staple
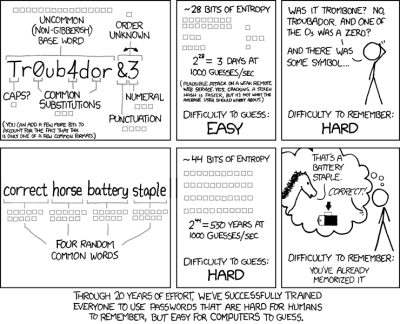
So we’ve established that password security theatre is a thing, so what are the alternatives? XKCD had a stab at it with “correct horse battery staple“, in which they put forward the idea of picking four memorable words to make a much longer password with greater entropy because of its size. This is a great way to make a memorable password, but it deserves a closer look. The attacker has only to guess four things to crack it, but that’s still OK. Assuming the owner of the password is an Anglophone and taking a back of the envelope estimate of around 250,000 English words including obsolete ones then we calculate that there are 3.90625 × 10²¹ possibilities, which is better than our random 10-character ASCII string.
The trouble is, the vocabulary of an average native English speaker is considerably less than the 250,000 figure. You can check yours here, but the average is around 20,000. When I worked for a well-known dictionary publisher we did the test and found most of us were in the 30,000 ballpark, with one specialist lexicographer colleague whose job was finding new words reaching an astounding 65,000. But if most users have 20,000 English words from which to pick their password, the number of tries drops to a more manageable 1.6 × 10¹⁷. Given that it’s more likely they will pick words with a higher frequency in the language that figure drops even further, and as they’ll tend to form a sentence rather than a random sequence the attacker can narrow down their choices even more. Are you still happy with your accurate equine power source fastener now?
Just How Far Do You Need To Go?
So the more we look at password security, the more it becomes evident that the whole edifice is built on foundations of sand. But should it be our only defence? Of course not, and we’re sure that most readers will already be using two-factor authentication, in which something you have as well as something you know becomes a factor. For many that’s a cellphone rather than a security key, but even then there’s the prospect of a miscreant hijacking your number. Is nowhere safe? Perhaps it’s time to dial back the paranoia.
There are probably several levels of service for which you need a password. Ones that don’t matter, ones that would be a mild PITA if cracked, ones that would be a major PITA, and ones that would be game over. And in turn there are several classes of attacker which you can probably classify by level of resources and by willingness to put in the work.
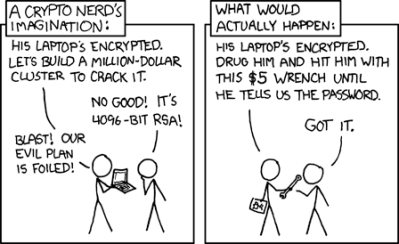
If a government agency wants your password they’ve already been through everything in your life and found it, or more likely they’ll haul you into jail and hit you with a wrench until you tell them. Likewise your local hoodlums, except they won’t bother hauling you into jail before breaking out the wrench. Scammers in a country far away will have you give it to them through a phishing scam or a piece of malware if you’re unwary enough to fall for them. Which leaves the shadowy hoodie-wearing “hackers” beloved of popular media, who will use the techniques described above on password hashes in leaked databases.
It’s clear that password security is something we all need to have on our minds, and that using two-factor authentication with regularly changed unique and entropic passwords is probably about as good as it gets without descending into paranoia. But there’s still the problem of remembering passwords for hundreds of different sites, unless you simply reset the forgotten password with another arbitrary string every time you need to use one of the less-important ones. Has the LastPass incident put paid to the use of such services, or is that just more paranoia? Maybe it’s time to revert to the most secure method of them all, and write hem on the Post-It note under your keyboard.
0 Commentaires