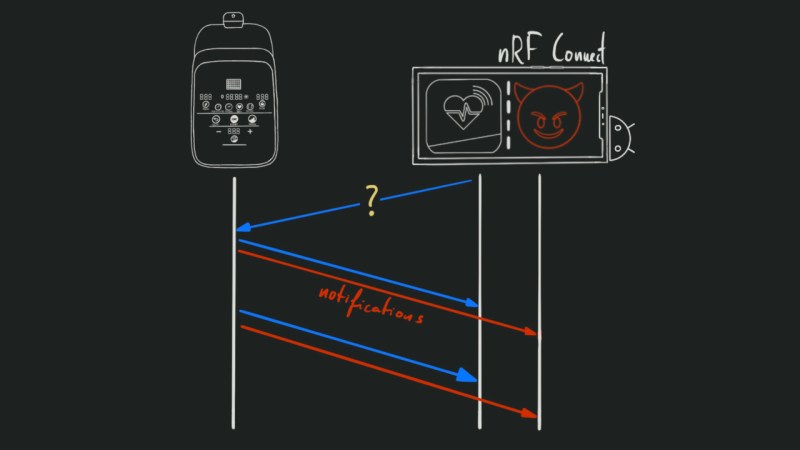
It’s a story we’ve heard many times before: if you want to get your data from the Domyos EL500 elliptical trainer, you need to use a proprietary smartphone application that talks to the device over Bluetooth Low-Energy (BLE). To add insult to injury, the only way to the software will export your workout information is by producing a JPG image of a graph. This just won’t do, so [Juan Carlos Jiménez] gives us yet another extensive write-up, which provides an excellent introduction to practical BLE hacking.
He walks us through BLE GATT (Generic Attribute Profile), the most common way such devices work, different stages of the connection process, and the tools you can use for sniffing an active connection. Then [Juan] shows us a few captured messages, how to figure out packet types, and moves into the tastiest part — using an ESP32 to man-in-the-middle (MITM) the connection.
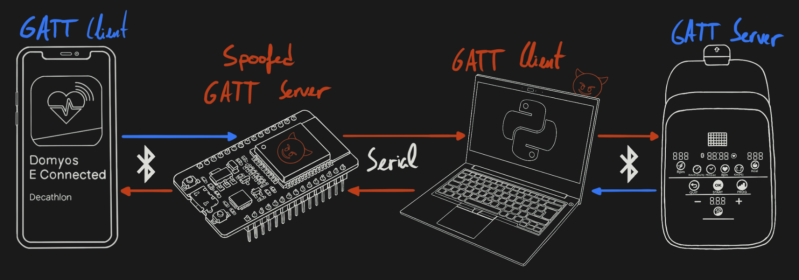
The MITM consists of two parts: a laptop with a Python script talking with the Domyos EL500, and an ESP32 that’s spoofing the EL500 to a smartphone app, tied together with a serial link. You can capture all the messages that the app and the trainer are exchanging, modify them in real-time and see the reaction, and figure out how to extract all the data you could dream of. This is more than enough to conquer the next frontier — writing a third-party app to capture workout data, and we can’t wait to see this experiment conclude.
BLE is ubiquitous and used in what feels to be every IoT device under the sun, which makes it all the more wonderful that we’ve got yet another tutorial on how to bend it to our will. The tools are easy to find, too. You can use an ESP32, a Raspberry Pi, or an nRF dongle. You can even get pretty far using nothing more exotic than an Android device. Whatever approach you take, the journey is sure to pay off.
0 Commentaires