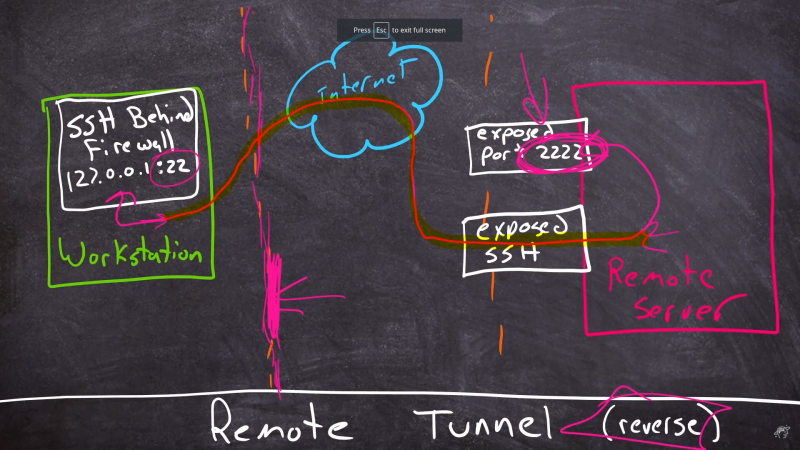
Once upon a time, I was doing on-site support for a hardware install at a hotel a few years ago. The remote tech’s remote desktop software didn’t want to play with my Linux laptop, so he couldn’t get into the switch he needed to configure, to make the install work. I asked if it had an SSH port he could use, were he were in the room with me. Of course it did, but that didn’t do him much good. I ran a reverse SSH tunnel out to my public server, and pointed it at the switch on the local side. I convinced him to SSH to my server on the given port, and he was magically connected to his switch. He was literally in awe of that trick, and demanded to know how it could be done. SSH is magical, but tunneling traffic over SSH is straight-up wizardry. [Shawn Powers] agrees, and decided to help the rest of us understand the process.
There are two basic ways to launch a tunnel, the first being a local tunnel, that listens on the local machine, and forwards it to the remote machine. On the other hand, a remote tunnel will listen on the remote machine, and deliver the traffic to the local machine. The real fun begins when you have multiple SSH sessions, and connect one tunnel to another, to route something just where you need it. For extra credit, check out the hidden SSH command line, by pressing Enter, then tilde and the C key, each one at a time. Also for extra credit, check out the rest of [Shawn]’s Linux content, to learn some extra Linux goodness.





0 Commentaires